After a long wait, Apple finally officially announced the much-hyped AirTags. If you’re not familiar, AirTags are Apple’s response to industry leaders, such as Tile, and even established competitors such as Samsung.
AirTags can be placed onto any item you’d like to keep track of, such as keys or your wallet. While this technology is certain to alleviate issues with losing those hard to keep track of items, the means by which this new product works can present something of a security risk.
This article will break down how this new product works and how it may potentially compromise your privacy.
However, if you would like to get more advice on whether you should buy Airtags, take a look at our “Should you buy Airtags” article.
How Do AirTags Work?

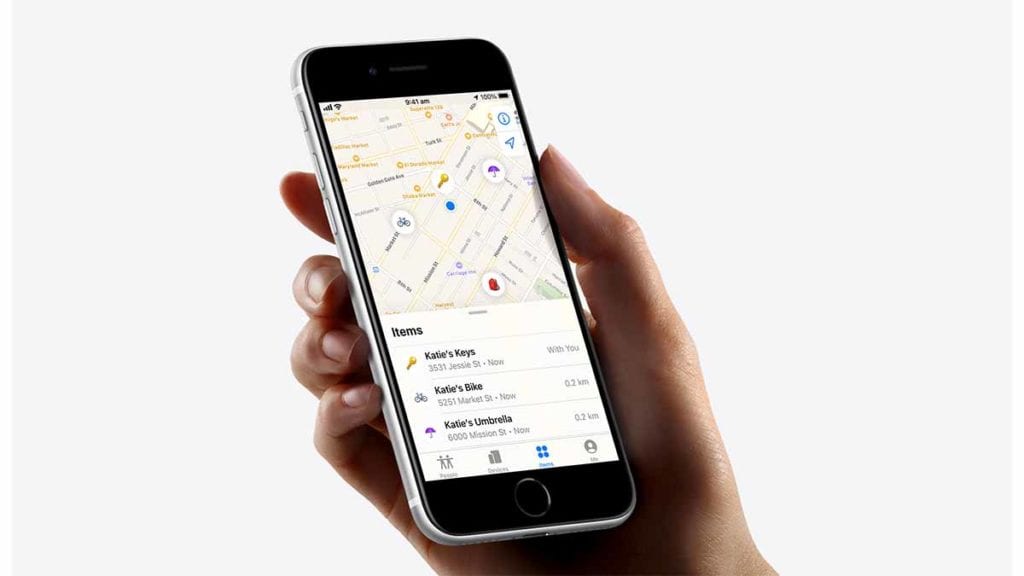
Similar to Tile, AirTags are a small metal disk that, once paired with your Apple ID, will periodically report its location to your Find My app. Every tag has a unique code that it transmits to any compatible phone within a 100-meter radius, which then transmits this information directly to Apple’s servers with its location data.
If the tag is paired to one of your devices, you’ll be able to check your Find My app and get a good idea of just where your tag is.
What makes this important is that the AirTags themselves lack any sort of positional location abilities: they do not have any sort of in-built GPS system, instead, they rely completely on this system of pinging nearby Bluetooth enabled devices and using those devices to estimate the Tag’s location.

On top of Bluetooth technology, Apple uses a new technology known as Ultra Wideband, which is compatible with newer iPhone models such as the 11 and the 12 and is useful in that it allows for very precise location tracking.
While the actual nature of the data collected, essentially just the tag ID and its location, isn’t a huge privacy concern, the massive scale in which the network operates can be worrying. Every single iPhone currently in use is out there listening in for AirTags, offering that information back to Apple’s services.
Another concern is data usage: while the amount of data used by this service isn’t that high, it’s something to be aware of if you are traveling internationally, as the last thing you’ll want is to get slapped with unexpected roaming charges.
Can AirTags be used for Stalking?
While the technology itself doesn’t lend itself to a major privacy issue, there are concerns that the actual functionality of it may be used for nefarious purposes such as stalking.
The AirTags are small, mobile, and discrete, making them very easy to hide in a victim’s car, bags, or even their person. While this has always been an issue with other trackers such as Tile, Apple’s entrance into the market makes this fear much more realistic, as the Apple network is much larger than comparable products such as Tile, as Tile has just a few tens of thousands of users compared to Apple’s billion.
Apple claims that they have designed the AirTag with this sort of thing in mind, with certain features designed to protect users from would-be stalkers. For example, AirTags give out an alert when they’re with a person who is not its owner.
This alert will come in two primary ways: as an audible alert to bring the AirTag’s existence to the awareness of the potential stalking victim, and a notification if they happen to have an iPhone as well.
However, these measures are not quite as secure as they’d seem. Some small experiments have shown that as long as the AirTag is connected frequently enough with the would-be stalker’s device, none of these measures would be triggered.
This means that as long as a would-be stalker connects their device to the AirTag once in a three-day period, none of these safeguards would alert the potential victim to the existence of the AirTag.
This issue is particularly concerning if you’re someone that uses a non-iPhone, because three days is a long time to be tracked before becoming aware of the AirTag’s existence.
This is very damaging from a privacy perspective because in that window of time, a person’s home address or places that they frequent can be identified before the person is ever aware of the presence of the AirTag, and by then, the damage will have been done already.
In some cases, the tracking may even go on for longer, as it has been shown in some experiments that the speaker of the phone can be turned off, thereby preventing the AirTag from ever alerting the potential victim. Even in the event, the tone isn’t turned off, it is just 60 decibels, which may be too quiet for the hard of hearing.
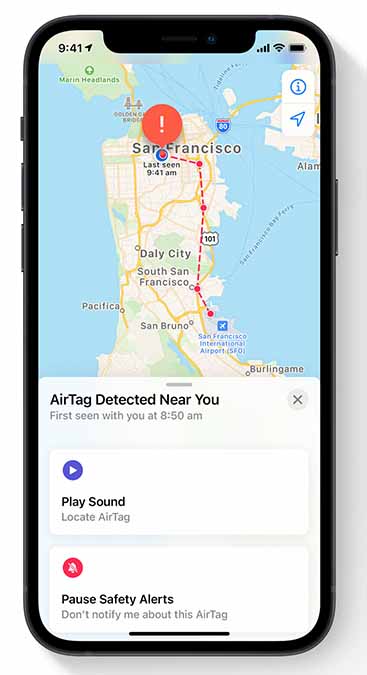
Another major problem is that these alerts can actually be turned off altogether, which presents a problem for a situation in which a person may be coerced into shutting off these alerts.
One other issue comes from the potential ubiquity of these items: as they become more and more commonplace, so will these alerts, and the likelihood that these alerts are simply ignored becomes likelier and likelier over time.
Another feature designed by Apple to help alleviate fears of being stalked is a little feature in the settings menu. If an iPhone user accesses their setting menu, they can search for unfamiliar AirTags.
If one doesn’t appear, the user can be assured that they are currently free of this problem. However, this does nothing to help people who use other brands of phones, as there is no app currently on the market to help Android users identify if they are being tracked with an AirTag.
Fortunately, Apple is planning on releasing an update that would assuage some of these concerns. Following this update, the AirTag is expected to randomly beep anywhere in an 8-24 hour window after being disconnected from the original owner’s phone, which is a much smaller window compared to the original three-day waiting period.
Apple’s AirTags are a welcome addition to the iOS ecosystem, especially to those of us that struggle with losing things. However, with this added convenience comes a security risk, one that hopefully can be addressed more fully in the future.





