It’s no secret that online privacy is becoming a thing of the past. From companies making billions of dollars from mining and selling your data, or scammers looking to take advantage of you. These are just some examples of the myriad of issues internet users face in the 21st century. This begs the question – what if there was a browser that could help?
What is Tor?
Tor (aka The Onion Router) has been a mainstay with the privacy and security enthusiast, a more reliable and private method to navigate the internet.
Used by anything ranging from a drug cartel to investigative journalists, computer geeks, and your average Joe, Tor should be an essential part of your digital privacy arsenal in a world where privacy is something that you can’t take for granted anymore.
Tor can trace its roots, not from a shady hacker group as you may suspect, but was initially developed by the U.S. Naval Research Lab and D.A.R.P.A. as a functional way to keep an eye on criminals without exposing themselves.

‘The Tor Project’ (the official, non-profit entity that now has ownership over Tor) receives donations from all kinds of reputable companies and federal (mainly U.S.) entities such as The National Space Foundation. The website and documentation of Tor lists all kinds of users and supports all major platforms (including even portable and even live instances). The likes of Edward Snowden have regarded it to be a reliable and effective tool to circumvent a majority of trackers and censorship.
How does it work?
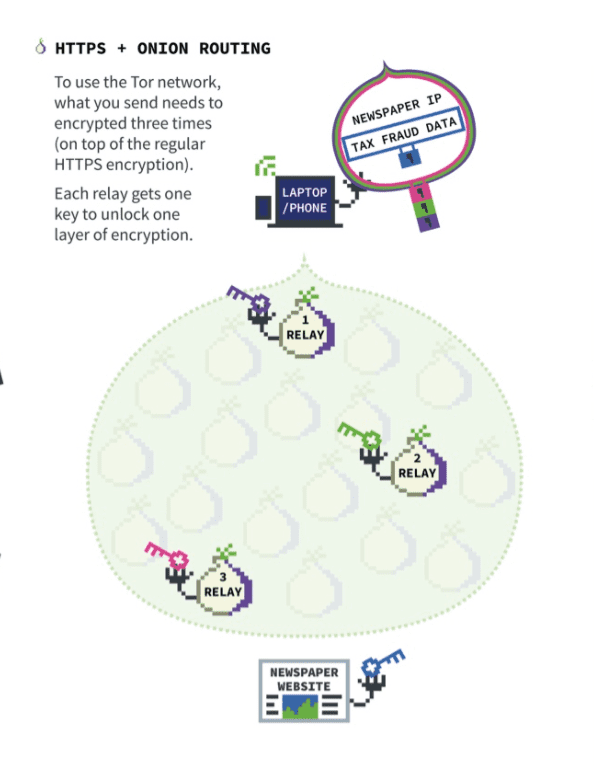
Tor uses a system that routes your Internet traffic through a series of intermediary nodes. Unlike a VPN, it doesn’t encrypt data. However, it makes it extremely difficult for anyone snooping into any one of these ‘nodes’ to figure out any identifiable information or where that data is going.
This system of nodes is run by a network of volunteers from around the world (and these ‘servers’ are all based in countries with freedom of information laws (such as Switzerland, Germany, Poland, etc.).
Your device first connects to the Tor network. It is assigned a ‘circuit’ (a randomly generated set of nodes calculated for latency and overall speed), with every packet after that being sent through these nodes is unidentifiable (both who is sending it and where it is going).
If you are running an Onion service, it enacts in the ‘rendevous point’, performing its function. It then continues to the ‘exit node’, where it will finally exit to the intended website.
Some great supporting services
As the initial request to the Tor network is unencrypted, I would personally recommend using a VPN to compliment Tor (if you are worried about your security, and you believe someone may be monitoring your network). A good option is Riseup, which offers a VPN that is proven to work in censored countries. They offer a free email service for people such as social activists.
Some other great services to use include (All of these are free and open-source, and are recommended by The Tor Project), onionshare (an open-source tool that allows for a secure (and anonymous) file exchange and to host websites, all while using the Tor network), securedrop (an open-source whistleblower submission system that media organizations and NGOs can install to accept documents from anonymous sources securely, and is protected through the Tor network). Another starting point is ricochetrefresh (a peer-to-peer (i.e., a decentralized network) messenger app that uses Tor and is meta-data free (i.e., has no identifiable information in each message).
I would recommend looking at TailsOS at tails.boum.org. It is a portable Linux distribution that allows you to take Tor on the go and secure any network. To have a look at some more services that are recommended, I implore you to check out The Tor Project’s own website at: community.torproject.org/onion-services/.
How to set it up
With the flexibility of Tor, it remains easy to set up and manage and does not bar its users to security experts or enthusiasts. These steps were performed on a Mac, although the setup process is the same on Windows. Still, installing Linux is a bit different. I will touch on that later on.
On IOS and Android, they have their respective apps, being: onion-browser (Onion Browser on IOS, be aware that although the Tor Project does not officially make this, it is recommended by them, and is created by someone who has been a part of the Tor Project for a very long time), and tor browser (for Android, this is made officially by the Tor Project).
Be wary not to use any other ‘Tor’ browsers, as they are not official and may not be using the Tor network at all or may be tracking you. These browsers are proven to be reliable and are also recommended by the Tor Project for use.
Installation Guide
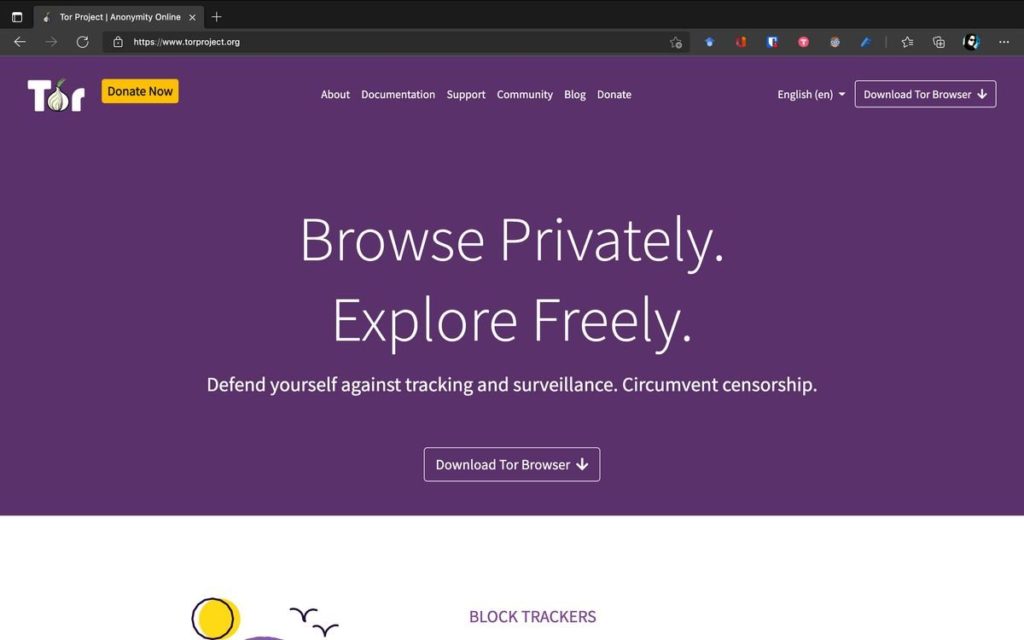
Your first step is to go to torproject.org (the official website to download Tor, if you download from an alternative website, you risk installing malware or the software being tampered with). Make sure you are using HTTPS (a secure protocol), and if you have access to one, a VPN.
After clicking on the ‘Download Tor Browser’ button, you will be redirected to a different page. Click on the package that suits your operating system. Here the paths split, and I will cover macOS/Windows and Linux separately.
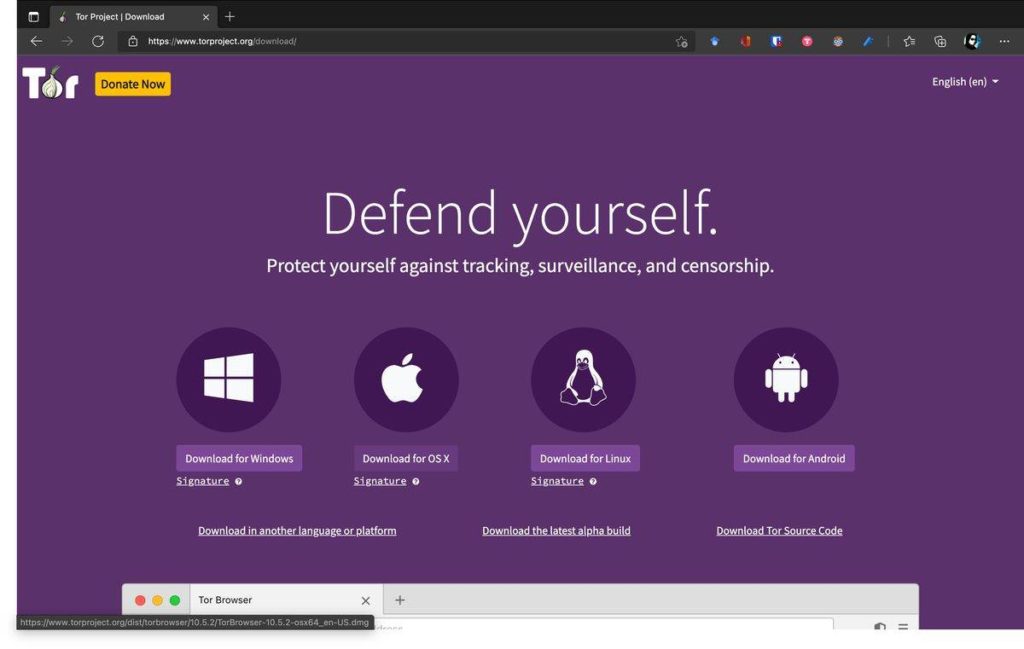
MacOS/Windows
In the popup that follows, press save/open (depends if you wish to keep the installer).
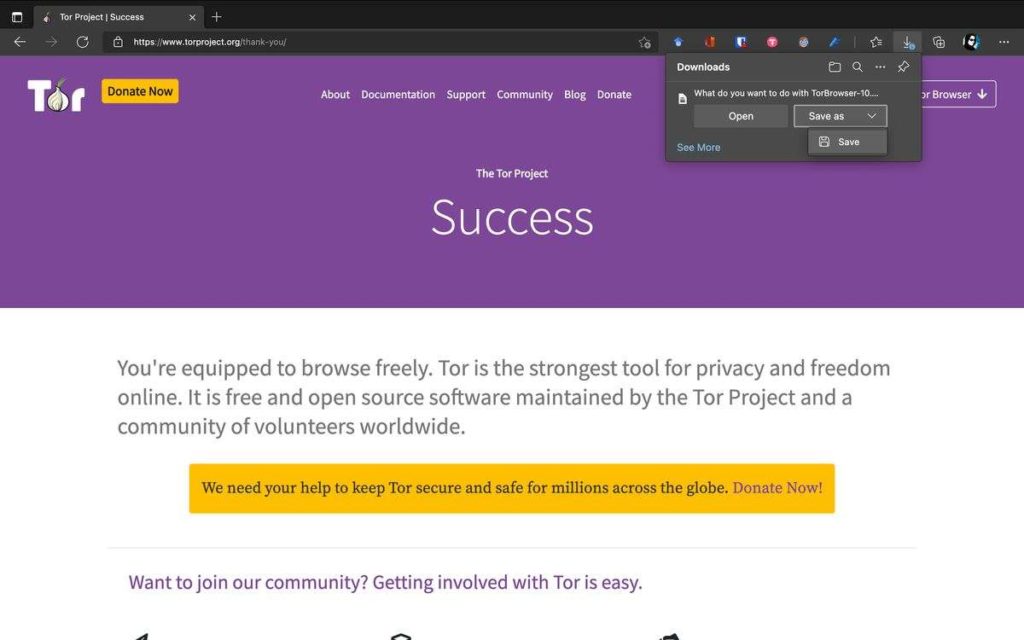
Depending on if you are on Windows or macOS, your installation process will differ slightly, but both will be done through a self-guided GUI.
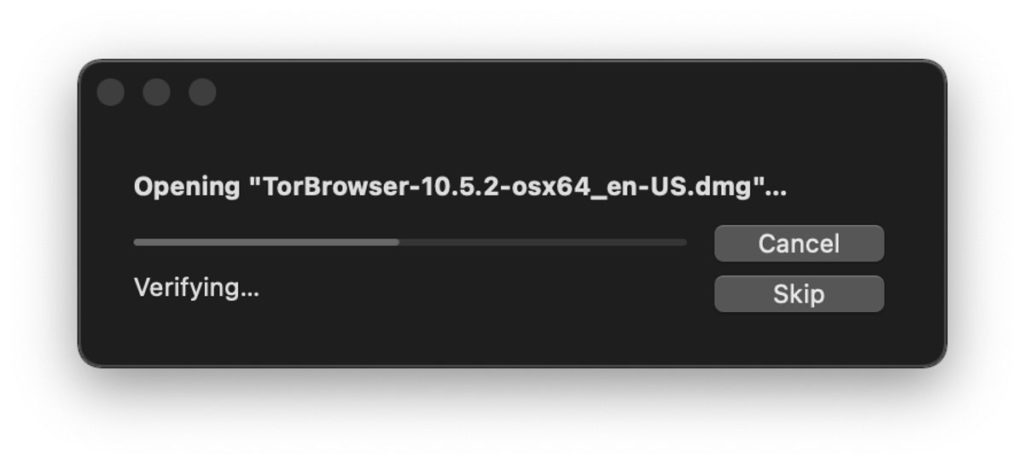
At first, there will be a portion where it will verify the download and installer, and if you are in Windows, it will give you the option to choose your install location. In macOS, you will see the following screen.

Drag the Tor Browser icon to the Applications folder (as in the standard app installation). This will then install the program to your computer.
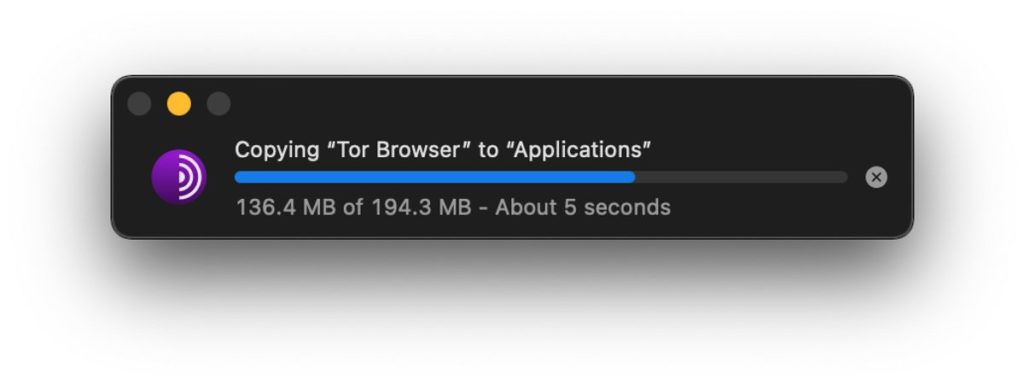
Drag the Tor Browser icon to the Applications folder (as in the standard app installation). This will then install the program to your computer.
Installing on Linux
Install the .tar.xz file provided by The Tor Project and then launch your preferred terminal emulator (which can be done by pressing ctrl + alt + t). I recommend using Bash for the installation (although I have tested using both Zsh and Fish). Make sure to note the setup folder’s name ( in my example, it is tor-browser-linux64-10.5.2_en-US.tar.xz ).
First of all, change your directory to where your installation files are located (usually in your ‘Downloads’ folder). Copy and paste the command below:
cd Downloads/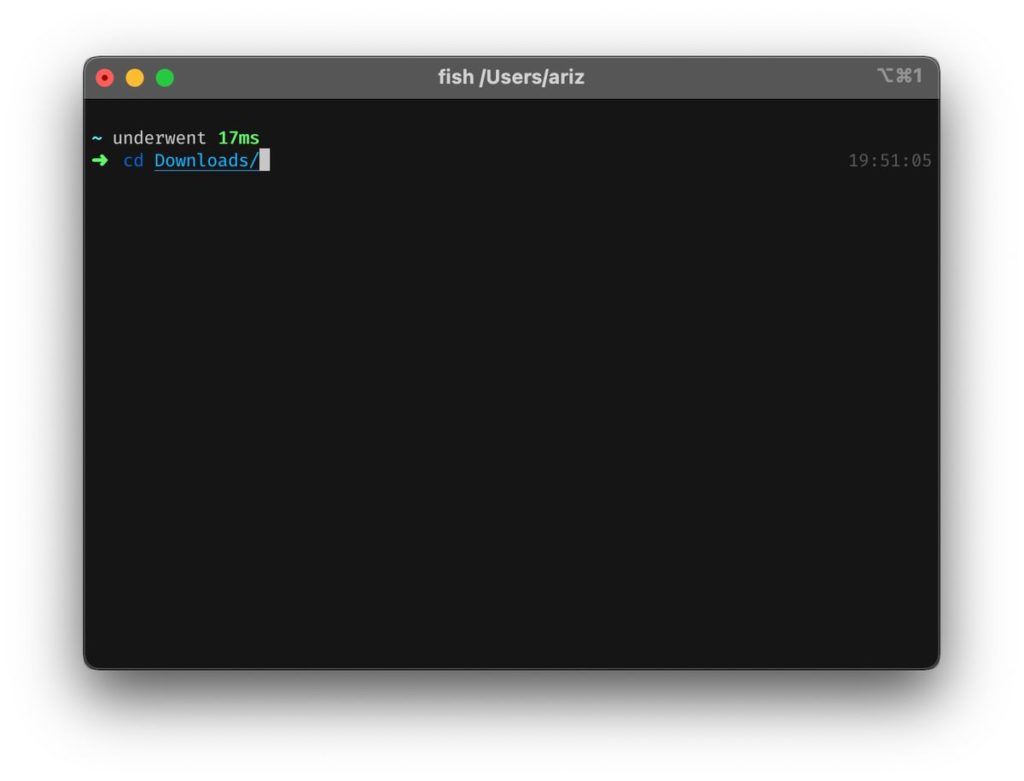
In my case, I installed it to a separate folder within my Downloads, so I am navigating to it now.
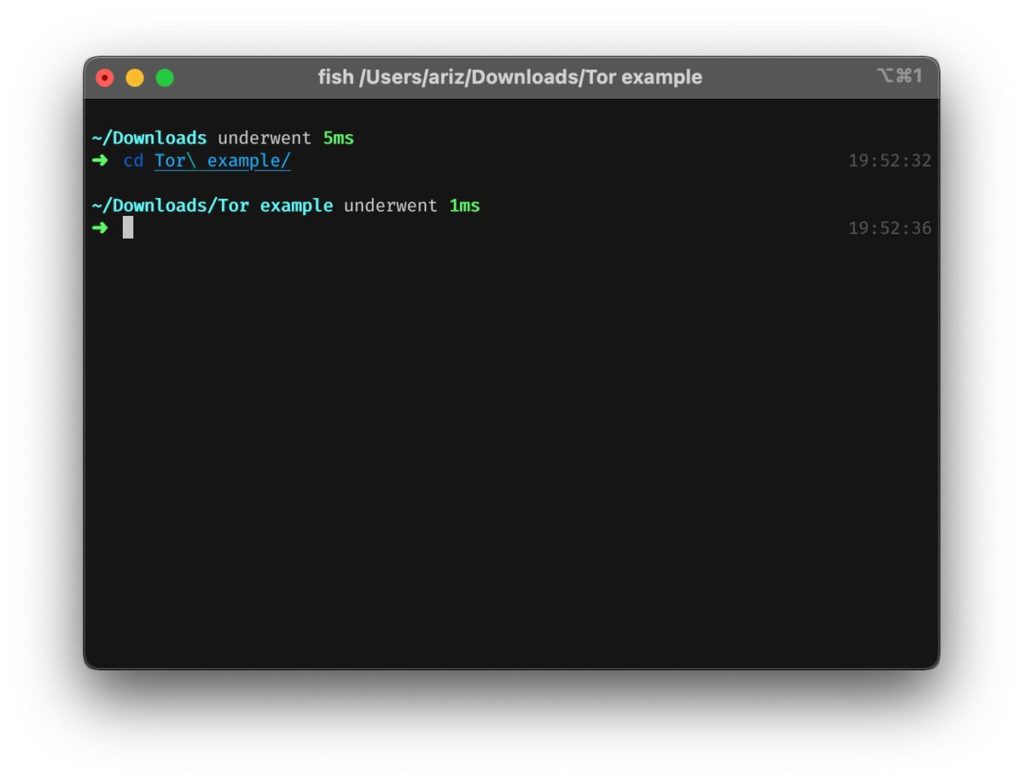
This is where you can use the file name that you noted earlier.
tar -xvJf tor-browser-linux64-10.5.2_en-us.tar.xzThe example that I have supplied uses the latest version when writing this article, although you should use your own folder. You can also use your autocomplete function (if you are using Zsh or Fish to make this process easier).
After typing in the command, press enter and let it run. You will see a lot of scrolling text as your computer expands the compressed files.
When it is done, you will see a prompt where you can type in.
Change your directory to the browser’s directory using the following command:
cd tor-browser_en-USNote that the above command may change with your region and language, so supplement the command with your own region and language (by replacing en-US with whatever was at the end of your installation file).
After this, you will navigate to the executable file by putting in the following command:
./start-tor-browser.desktop
This should run the Tor Browser and test to see that it does launch. If it does not, try the above steps again, or try and download the installer again. To mark it as an application (and to therefore be able to launch it using any launcher, write the following command):
./start-tor-browser.desktop --register-app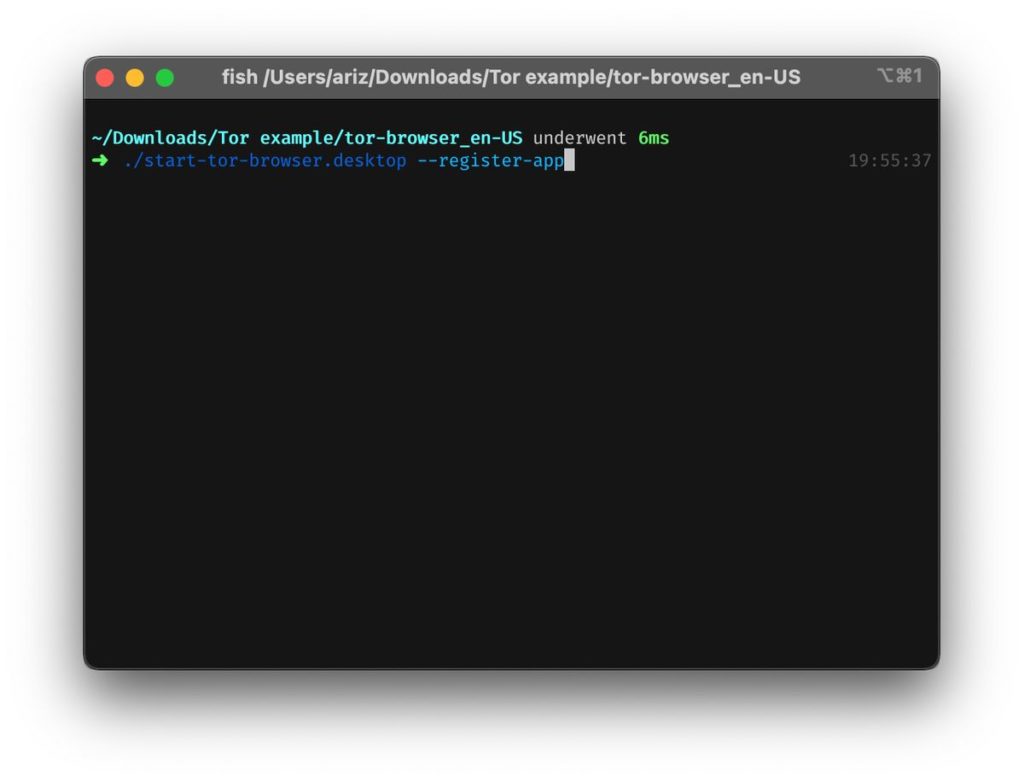
./start-tor-browser.desktop --register-appThis will make it accessible using any launcher. You can now continue with the setup process (which is universal). There are 2 main versions of Tor that you may encounter (an older and a newer version), and it may differ depending on your region which version you are given. I will cover both versions here and follow which version looks like the one that you have.
Ensure that if you end up moving the application, you redo this command in the directory to ensure that the link does not end up broken.
Setup Process for Older Versions of Tor
If you have an older version, it will appear with this splash-screen when you open the application.

Try pressing ‘connect’. If it connects, and you appear in the browser, you are done! If this doesn’t work, or if you need to connect to a proxy, or if Tor is censored in your country, keep on going by clicking the ‘configure button’
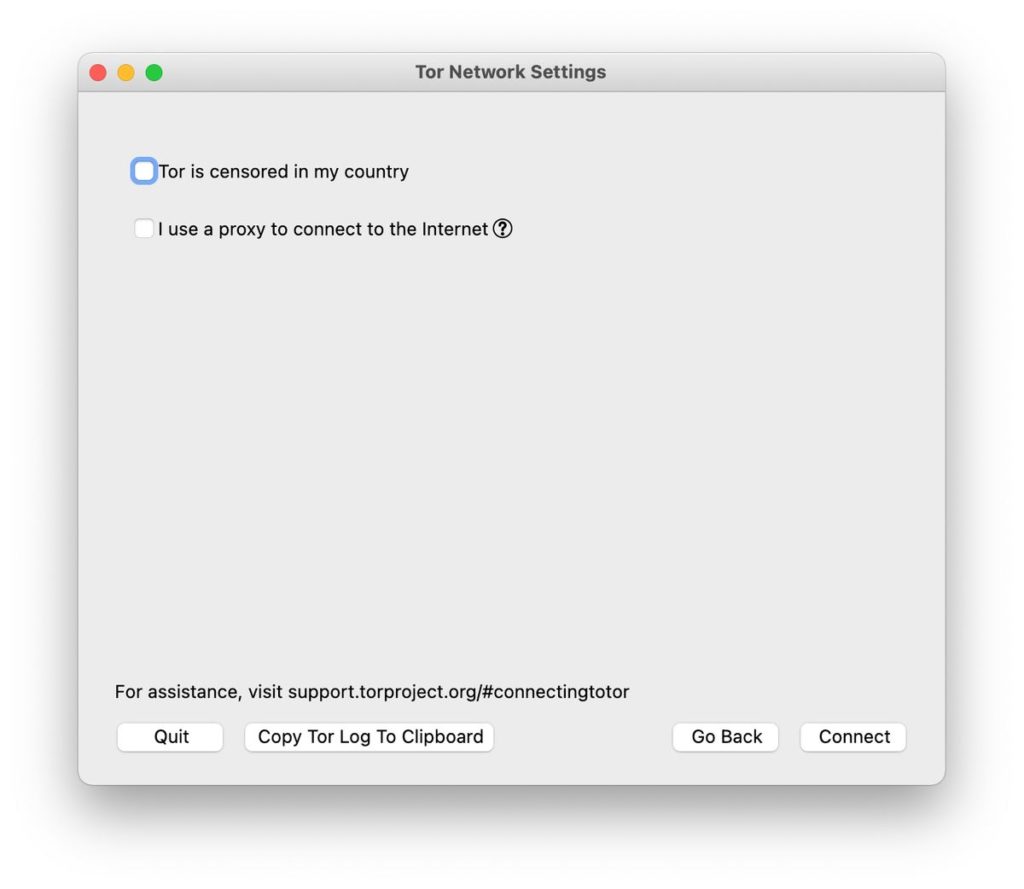
If your connection failed, or if Tor is censored in your country, check the ‘Tor is censored in my country’ box. The below is what you will see.
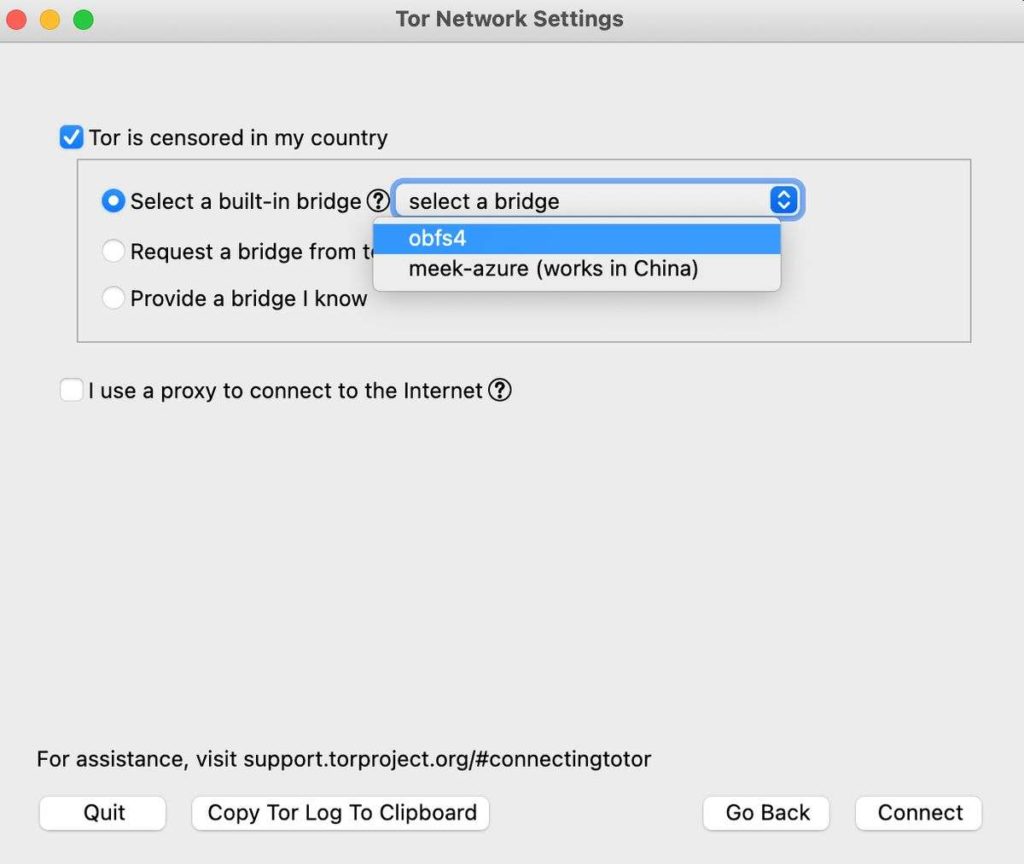
2 options are visible. These 2 options act as a method to bypass restrictions to your network by using a very secure proxy (obsf4) or using a proxy system to make it seem as if you are using a different ‘legal’ service like Google/Microsoft services (meek-azure).
This uses a built-in bridge to allow for you to connect to the Tor network (and is known through all installs of the browser). This slows down performance compared to without using the bridge.
I recommend using obsf4 for performance, although it is easier to tell you that you are using Tor if you are using meek-azure (which I recommend for outright security). If these also do not work (you can check by pressing the ‘connect’ button to test it out), you should then proceed to the next step by checking the ‘Request a bridge from torproject.org’. Note that these bridges only offer obsf4.
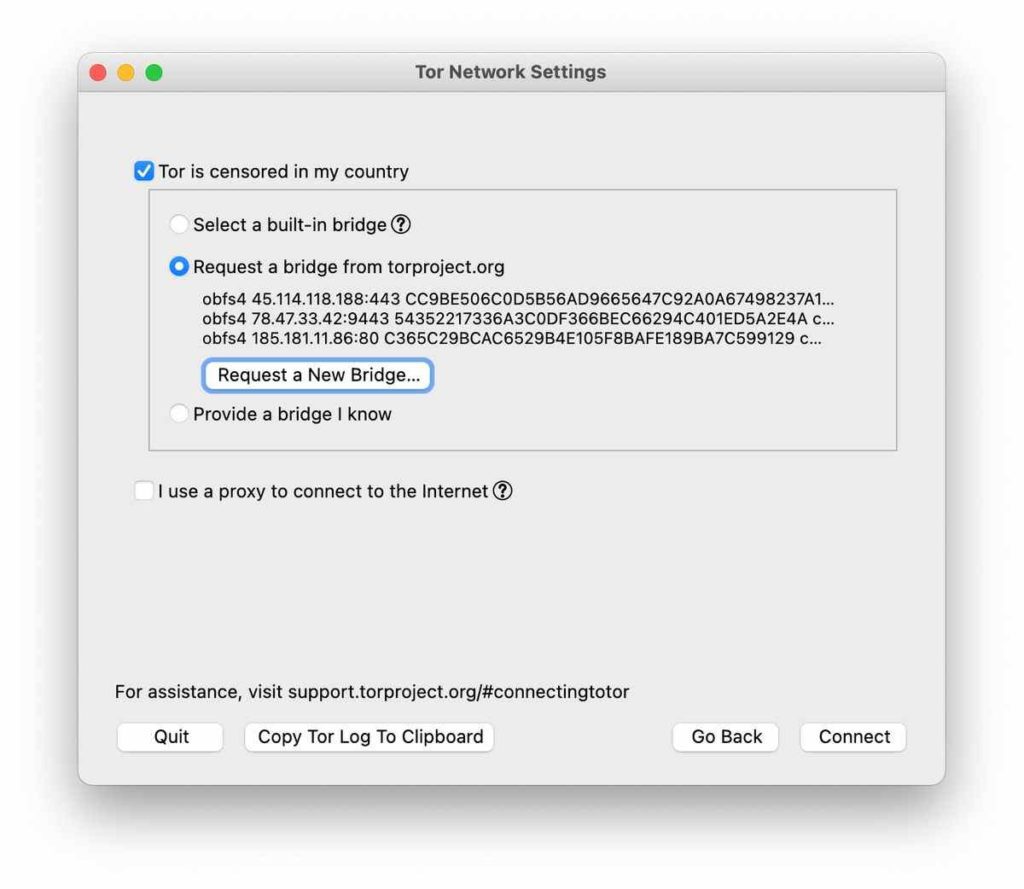
If you have requested a bridge before, it will show up here. If you have not, press the ‘request a new bridge’ button. You will see a CAPTCHA, which should be relatively simple to solve. If you cannot read the captcha, press the ‘refresh’ button to try a different one.
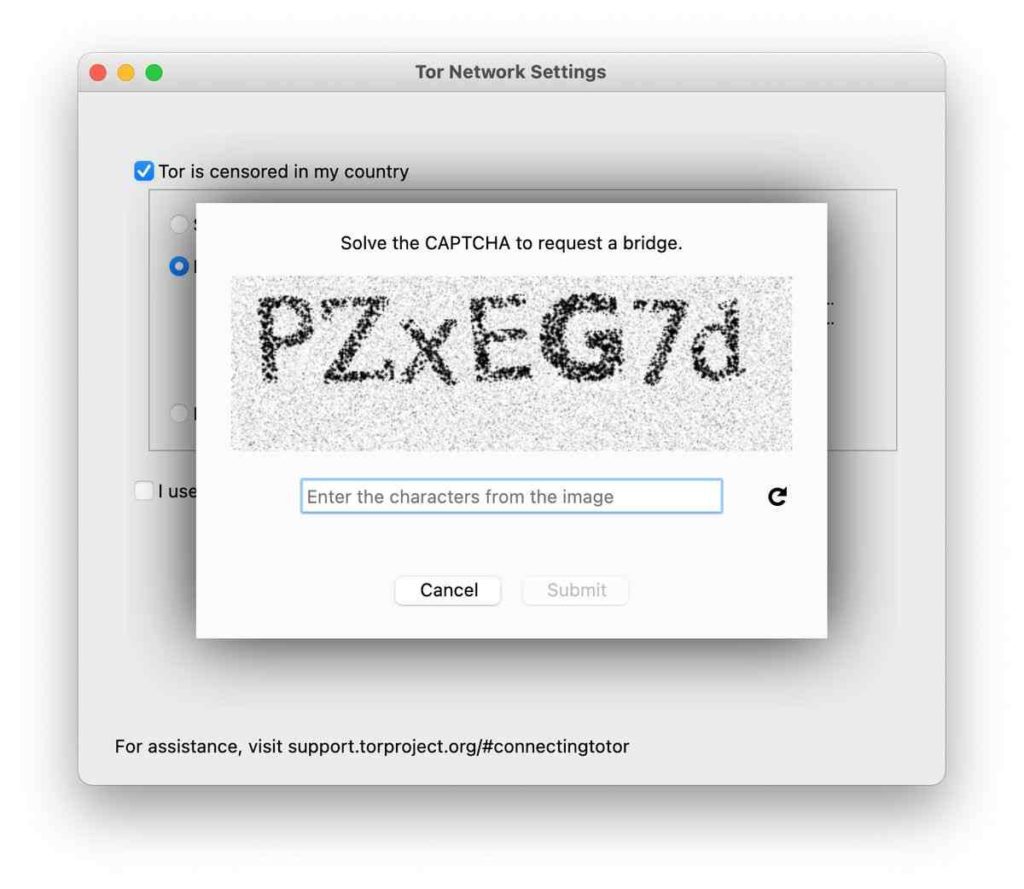
The bridges given here are private and, therefore, challenging to block (as they are not publicly listed anywhere). After this, you should receive some new bridges, and hopefully, you should be able to connect! If you need to connect through a proxy, check the ‘I use a proxy to connect to the internet’ box.
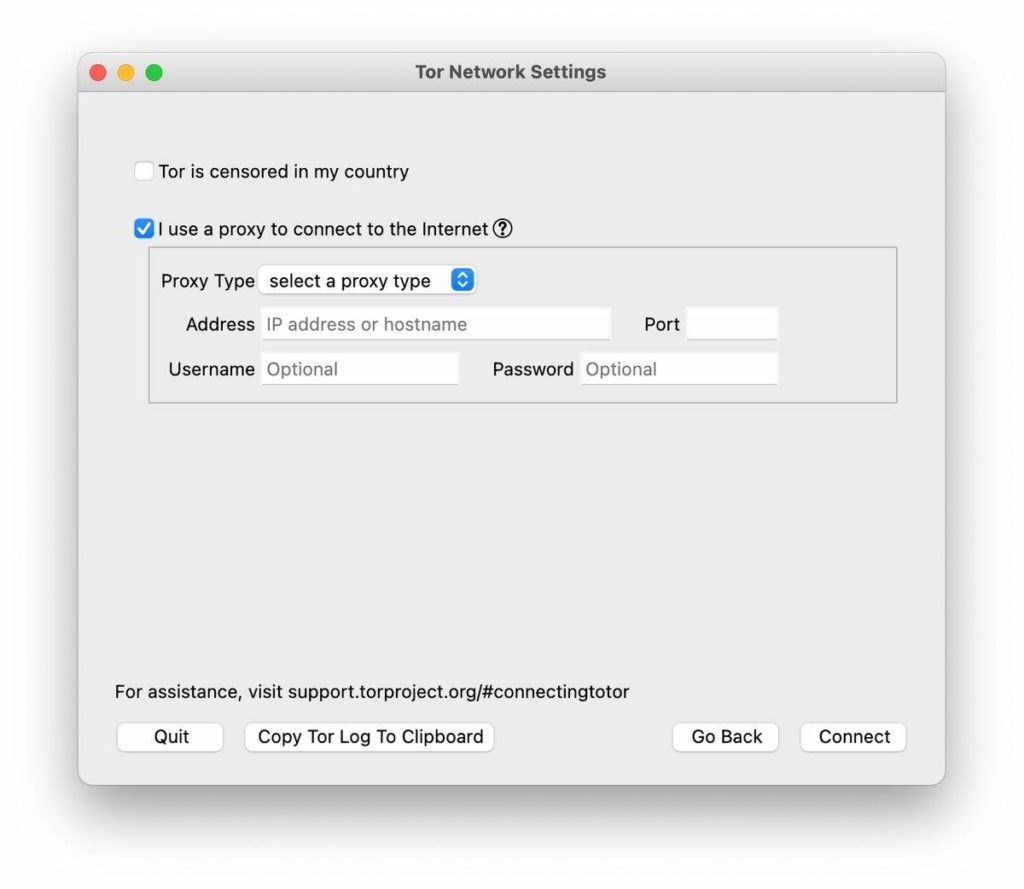
Fill in your proxy details here, and Tor should connect using your proxy. If your connection process has been successful, you will see the below as Tor establishes a connection.
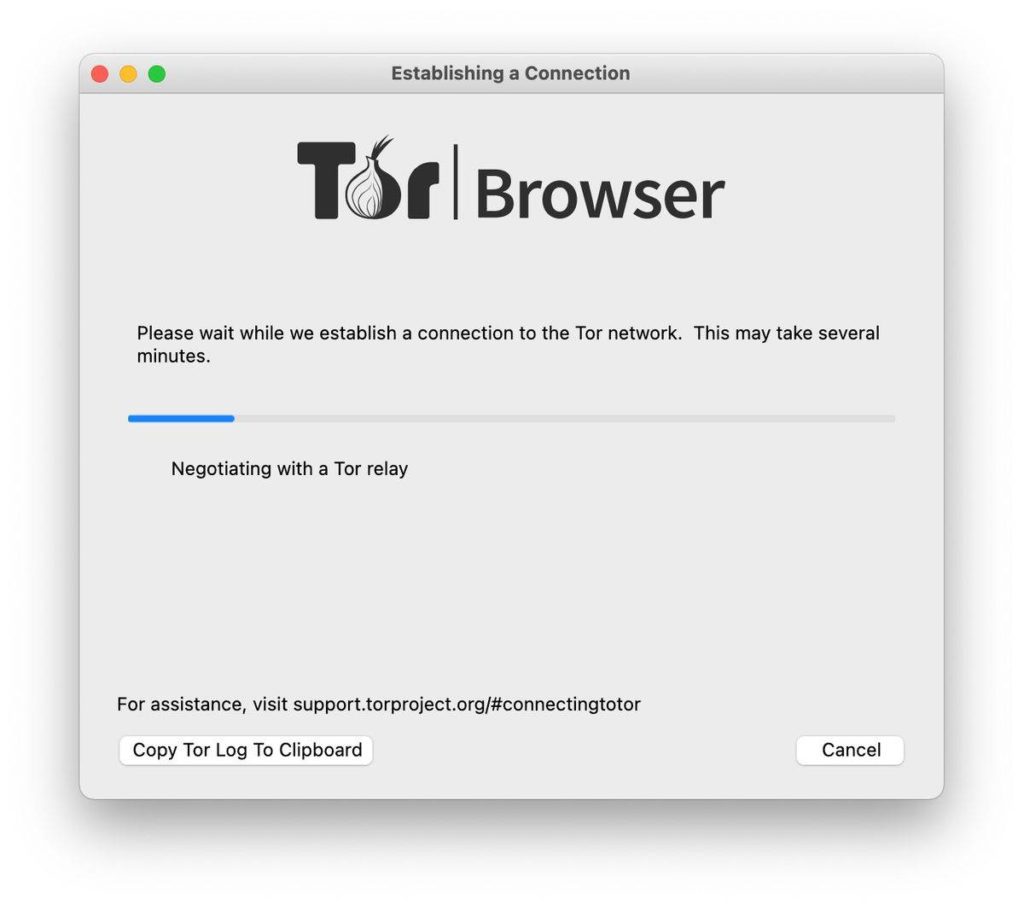
In this stage, the Tor Browser connects to the Tor network and establishes a connection with a relay (which allocates a circuit).
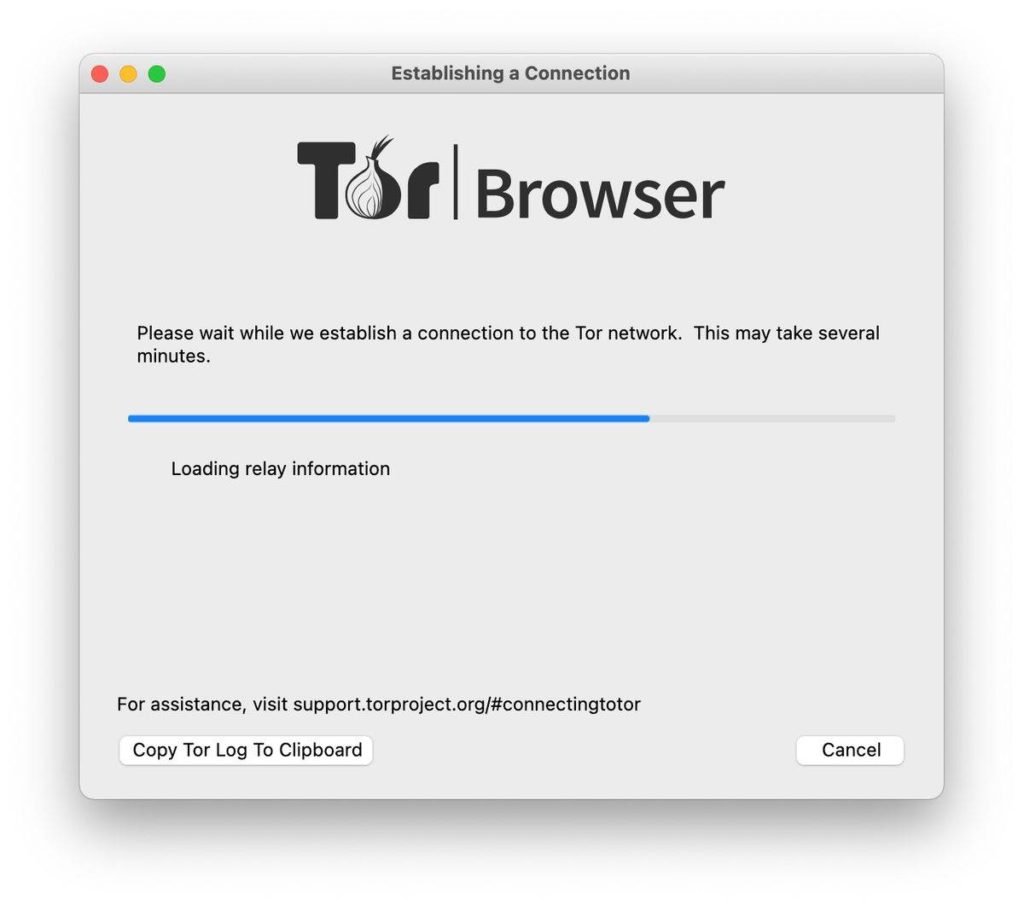
At this stage, the browser to loading information from the relay, which mainly involved securing a connection and making sure that the established connection is with the correct version of both the browser and the relay.
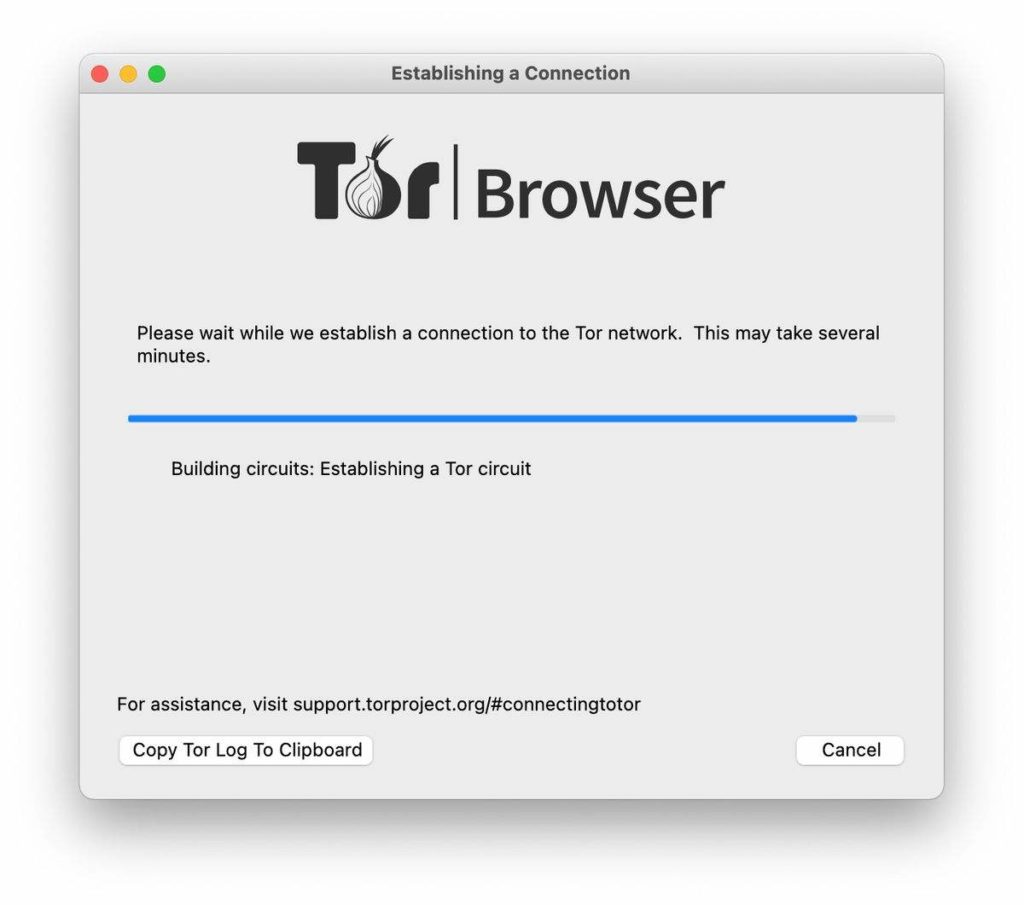
From here, it is just sitting tight until the circuit is completed, and you will end up in a new browser window. I recommend going to example.com to test if the connection works, and then visit whatever site you wish.
Newer Version
If you are using a newer version of Tor, your splash screen will look like the following:
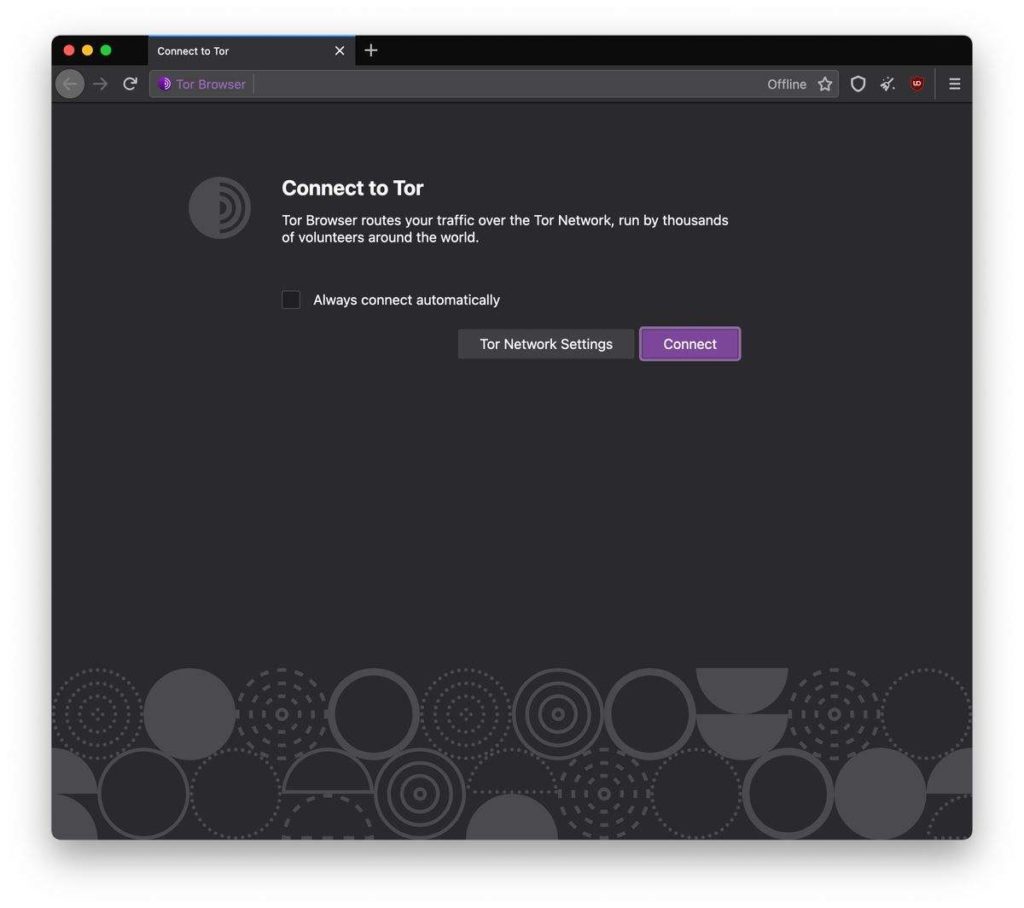
Try pressing ‘connect’. If it connects, and you appear in the browser, you are done! If this doesn’t work, or if you need to connect to a proxy, or if Tor is censored in your country, keep on going by clicking the ‘configure button’.
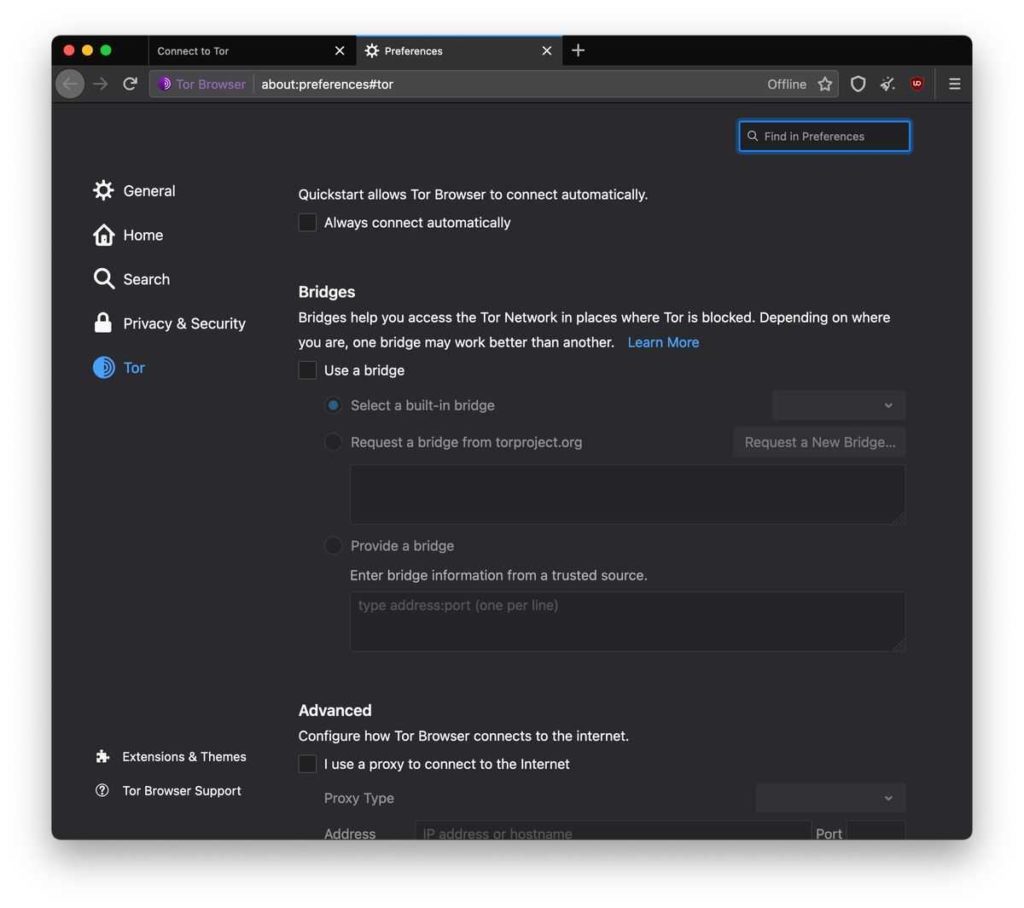
As you can see here, the interface here is more modern and tightly integrated with Firefox’s overall UI. If your connection failed, or if Tor is censored in your country, check the ‘Use a bridge’ box. The below is what you will see.
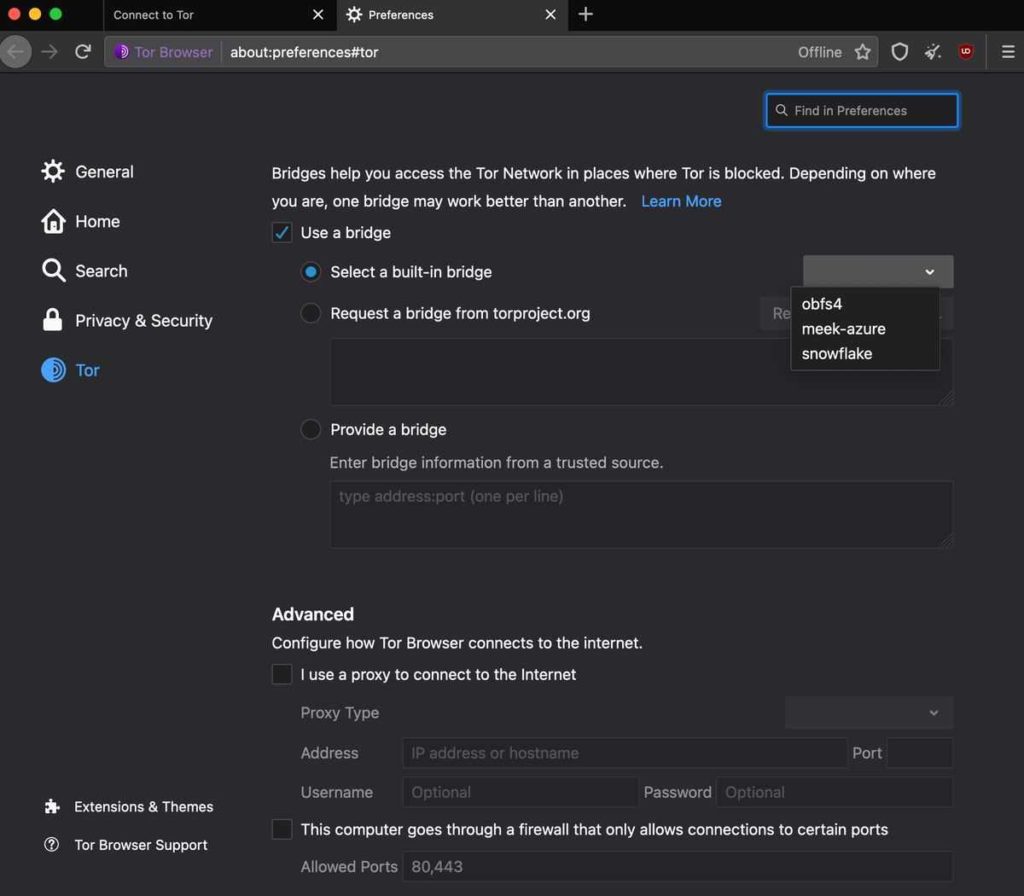
3 options are visible. These 3 options act as a method to bypass restrictions to your network by using a very secure proxy (obsf4) or using a proxy system to make it seem like you are using a different ‘legal’ service like Google/Microsoft services (meek-azure).
This uses a built-in bridge to allow you to connect to the Tor network (and is known through all installs of the browser). This slows down performance compared to without using the bridge. I recommend using obsf4 for performance, although it is easier to tell you that you are using Tor if you are using meek-azure (which I recommend for outright security).
A newer version of Tor also brings in the option for ‘snowflake’, which is an alternative proxy to obsf4 with a newer protocol. It is slightly quicker in my testing, although both obsf4 and snowflake are effective (although one may be more effective than the other in your situation, be sure to try both).
If these also do not work (you can check by pressing the ‘connect’ button to test it out), you should proceed to the next step by checking the ‘Request a bridge from torproject.org’. Note that these bridges only offer obsf4.
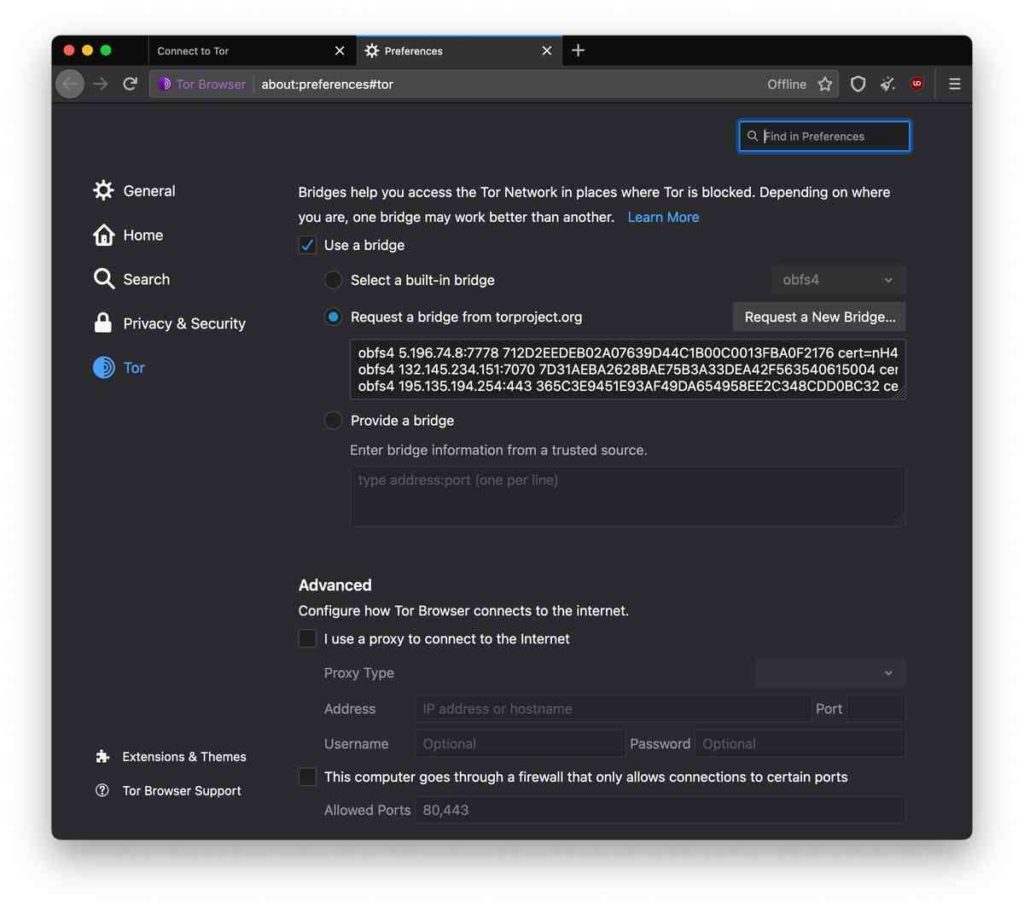
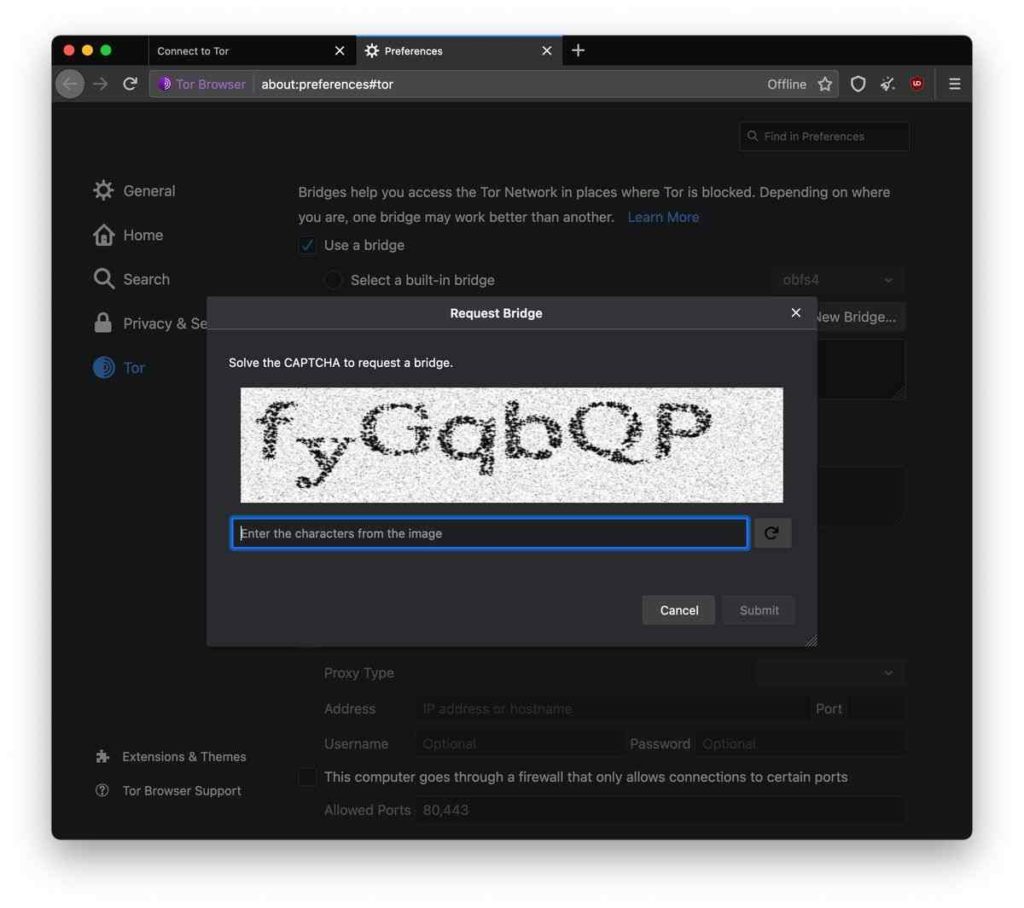
If you have requested a bridge before, it will show up here. If you have not, press the ‘request a new bridge’ button. You will see a CAPTCHA, which should be relatively simple to solve. If you cannot read the captcha, press the ‘refresh’ button to try a different one. It will then appear like the below.
The bridges given here are private and, therefore, challenging to block (as they are not publicly listed anywhere). After this, you should receive some new bridges, and hopefully, you should be able to connect! If you need to connect through a proxy, check the ‘I use a proxy to connect to the internet’ box.
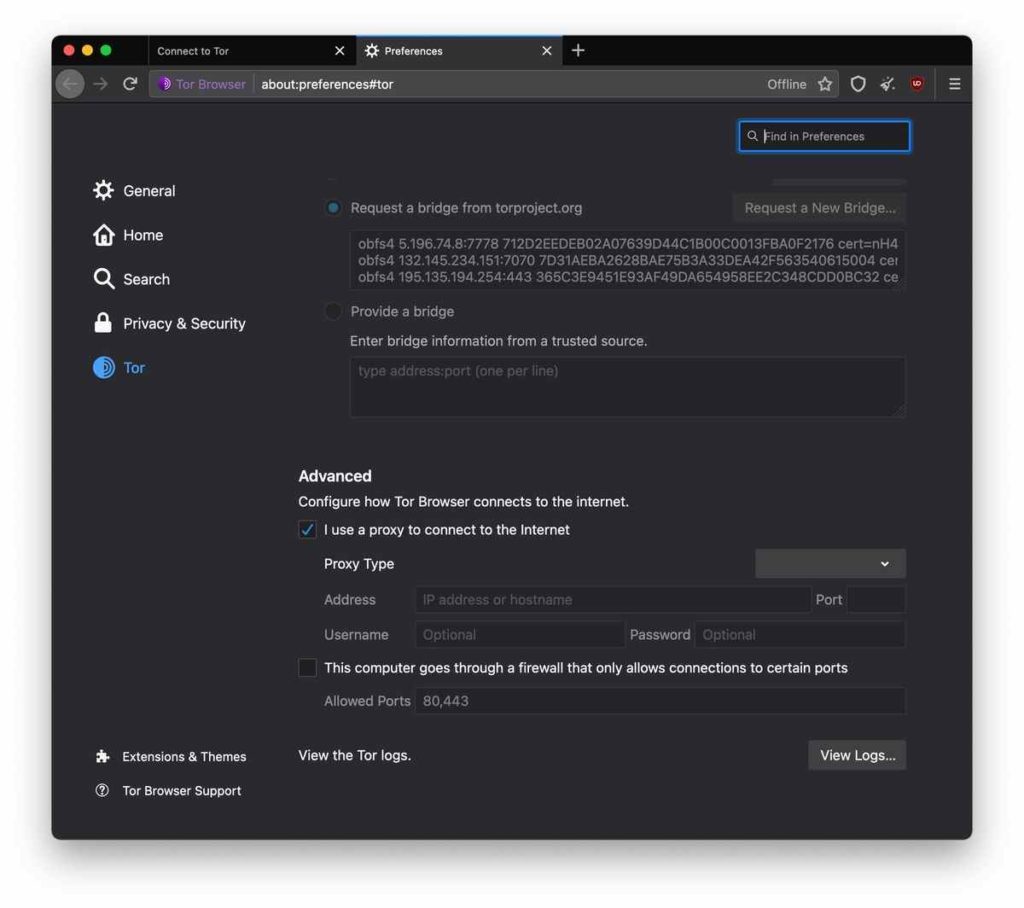
Fill in your proxy details here, and Tor should connect using your proxy. If your connection process has been successful, you will see the below as Tor establishes a connection.
As it is connecting, the search bar will have it written as ‘connecting…’. Make sure that this is present, as otherwise, it is not connecting, and you should try and relaunch the browser.
As it loads, there will be a progress bar, as can be seen below:
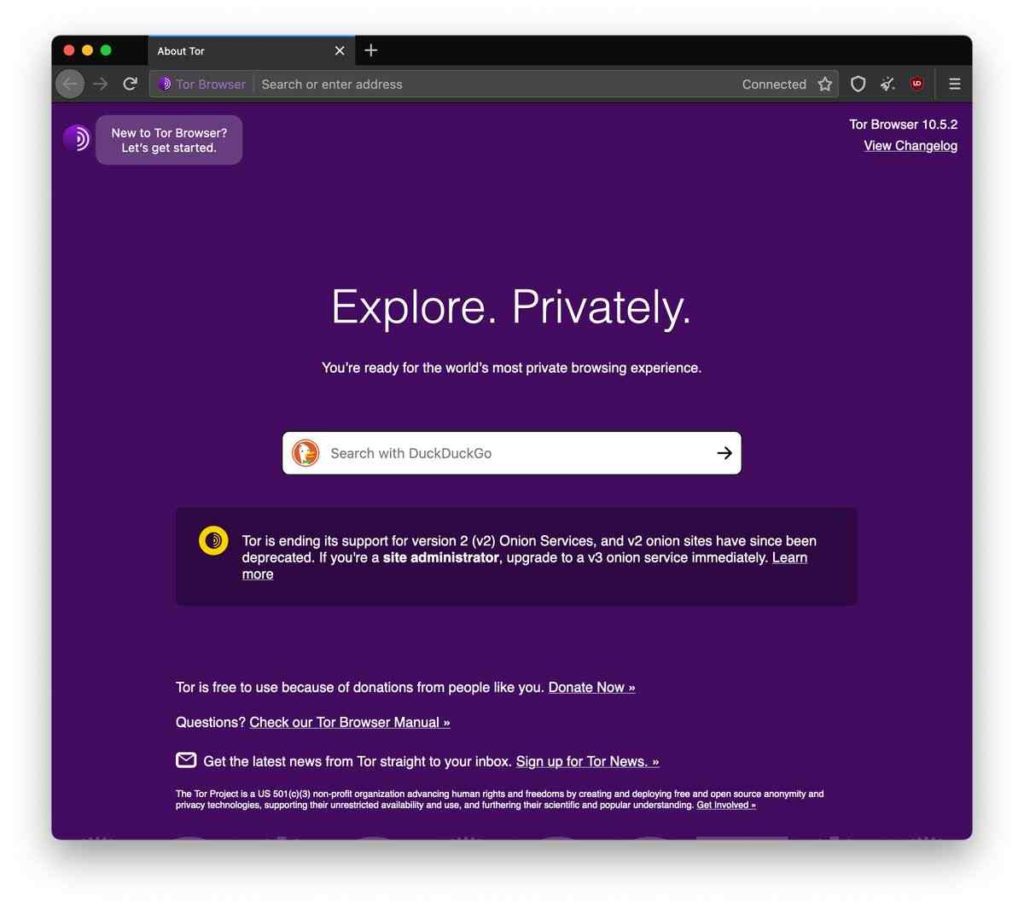
If the Tor browser can connect, you will see the browser screen appear
I recommend going to example.com to test if the connection works and then visit whatever site you wish.
What to do after the installation?
I recommend that you go to example.com to check if the connection works. This is as this has no geo-locking and is also a website that is easily accessible and easy to remember.
After this, you can go to whatever website or participate in whatever activity you wish.
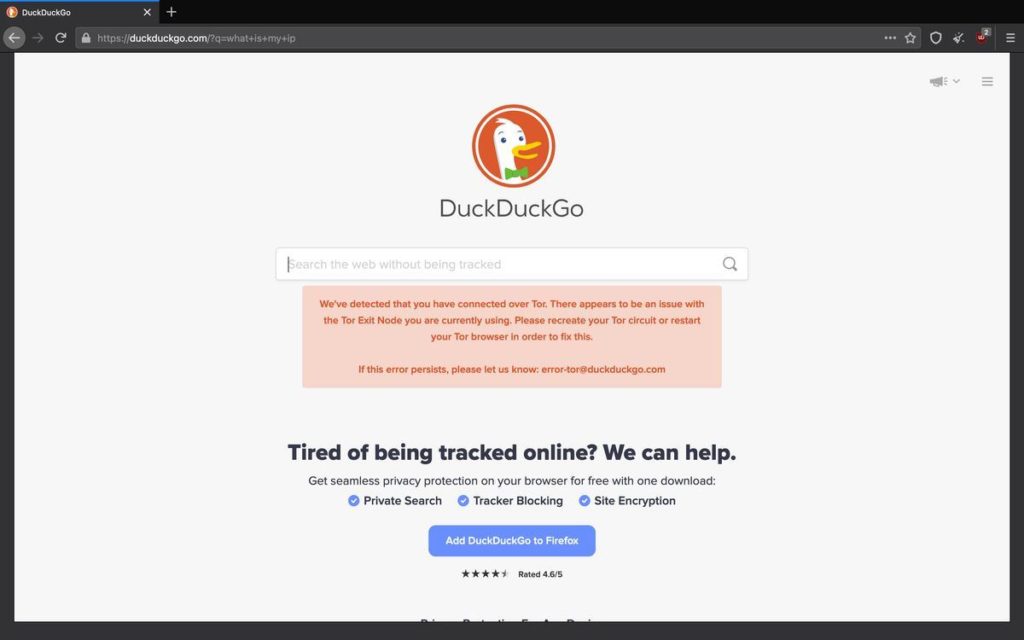
A note with the full-screen mode in Tor. As you can see here, it has little bars and does not use the full resolution. This is used as websites and organizations often track users by their resolution, and therefore Tor randomizes the resolution with every website to ensure that you are protected from tracking. Sometimes you can, however, got an error with the exit node, as pictured.
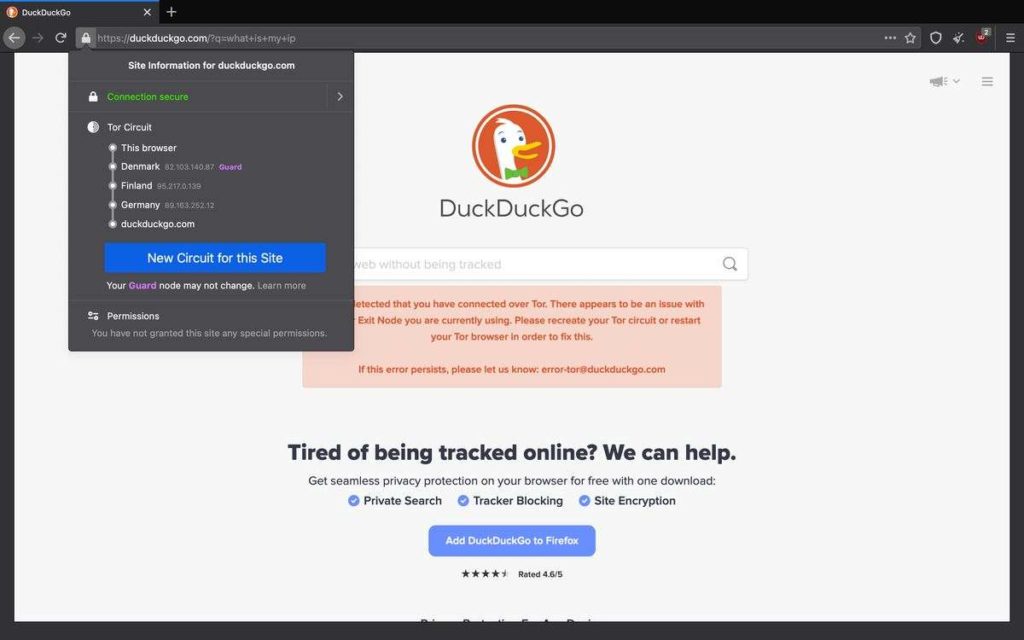
If so, you can refresh and change your circuit (and also view your circuit) by clicking on the padlock icon.
Press the ‘new circuit for this site’ button if you receive an error like this one.
Proving the security of the Tor network
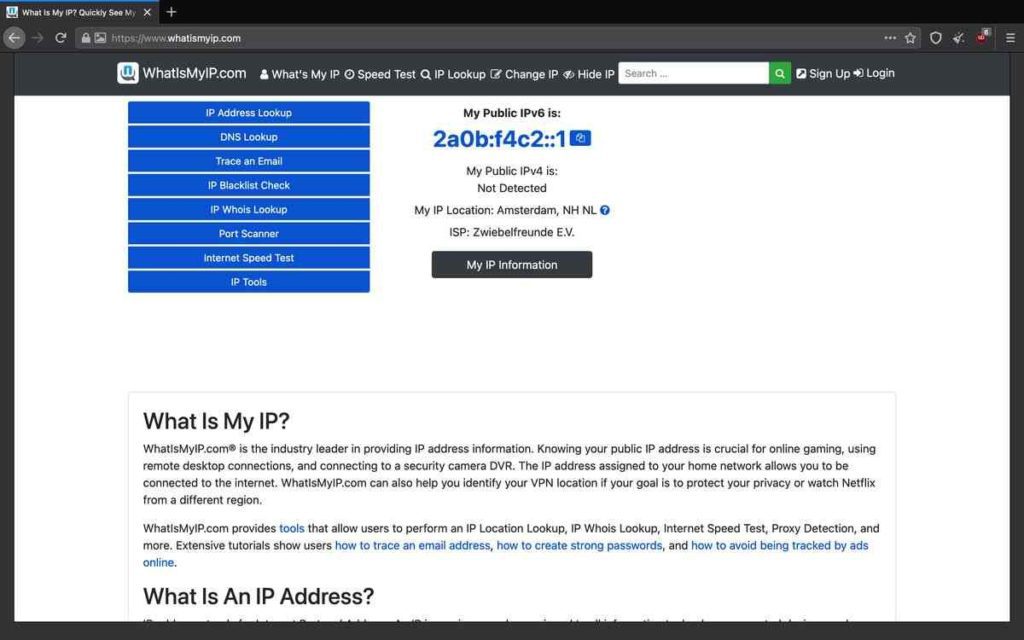
I have used 2 different tools to check if I can be tracked using the Tor network, as seen by using DuckDuckGo’s IP tool and whatismyip.com. As you can see, DuckDuckGo cannot get a valid IP address and thinks that my location is in Germany (although I am not in Germany).
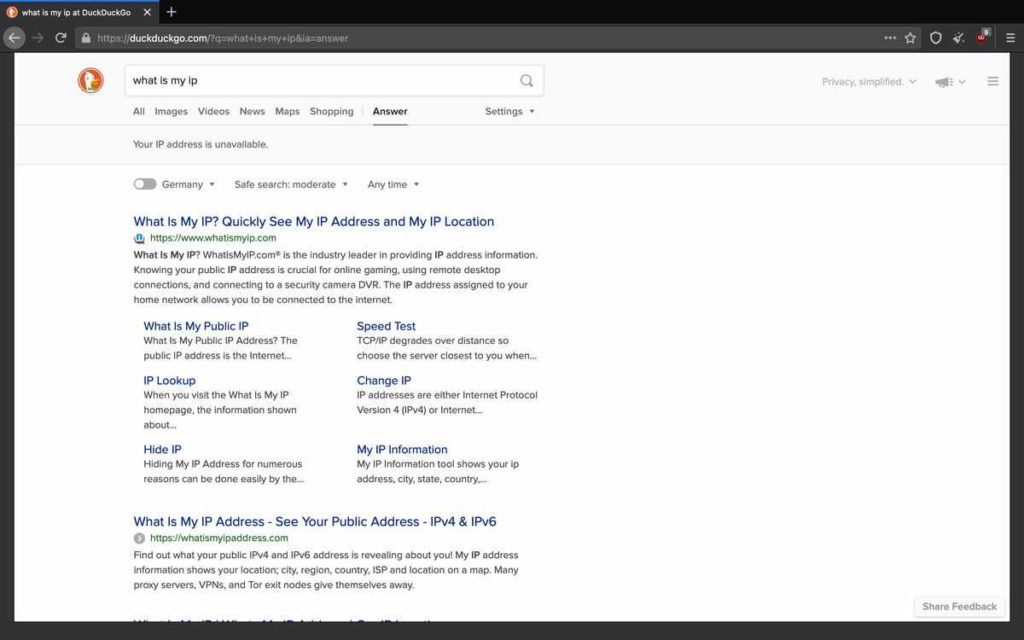
Double-checking using whatismyip.com , the results are the same, although this gives a spoofed IP address that is not valid. It further reinforces that the geolocation has been spoofed as well, as this comes up with Amsterdam (of which I am also not located in).
Tor essentially functions by routing your traffic through ‘layers’ of servers (hence the ‘onion’ name), and this can essentially spoof the information, as a server can only tell what happened with the server before it (think about it almost like a large game of Chinese Whispers, where the meaning/original meaning changes from one person to the next, and the original meaning only being revealed when the original messenger confirms it).
These servers are similar in function to a peer network, although they have the advantage of using the entire ‘world-wide-web, instead of websites and resources that are peer-based. Tor browser can work in the toughest of situations and has never let me down. It can work in nations with heavily censored networks while being discreet and difficult to track.
Is Tor worth it?
As seen in this article, Tor is one of the most secure ways to browse the web and is also done for free. It is recommended by Edward Snowden (a famous whistleblower of the CIA and security activist). I would recommend you give it a shot, and to browse away from the piercing eyes of ‘Big Brother’ and to stay away from the eyes of your Government or ISP. I hope this article has been helpful with your plunge into both Tor but the rabbit-hole of digital security.





